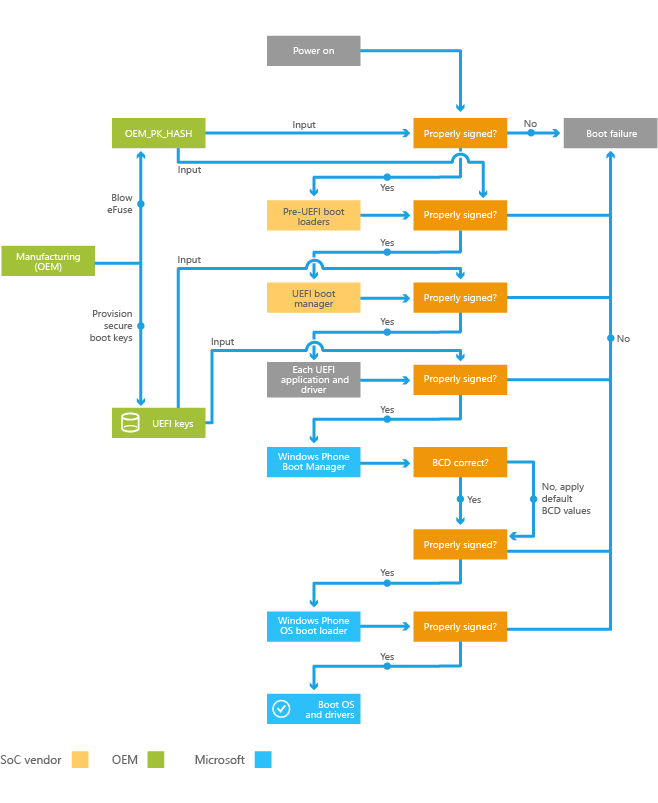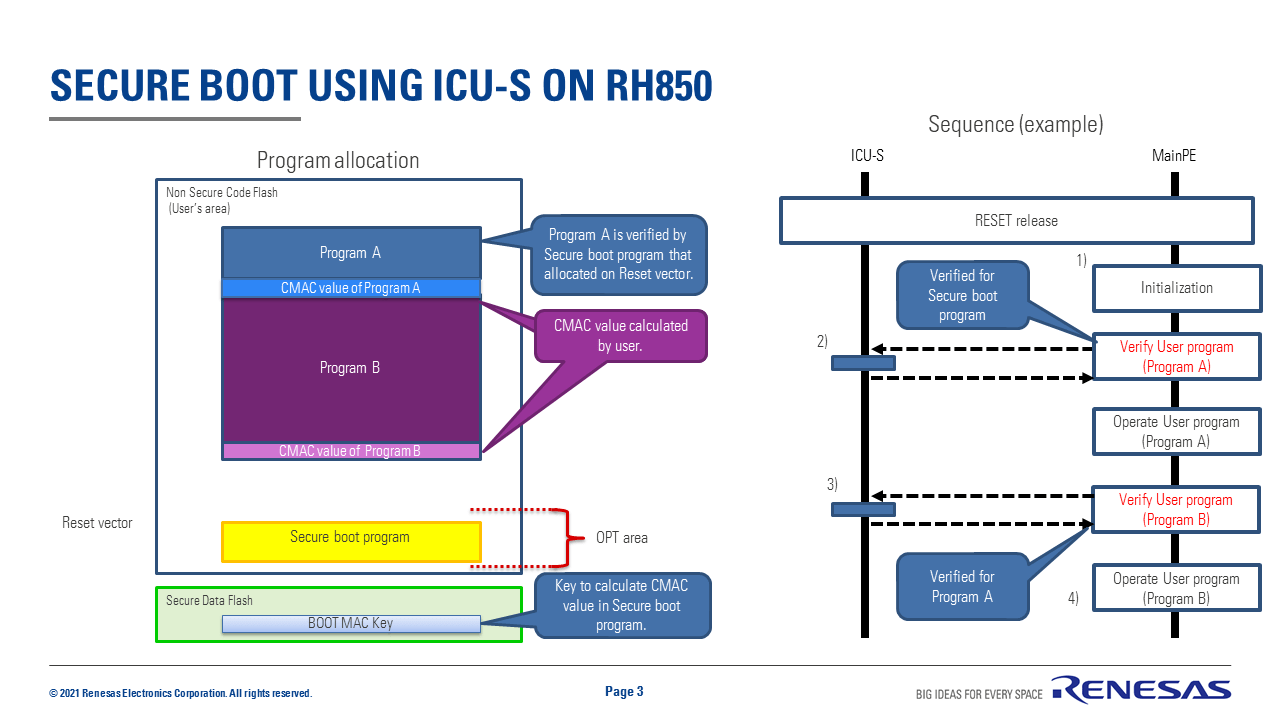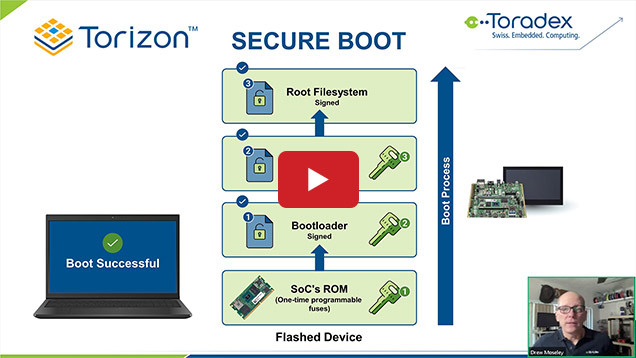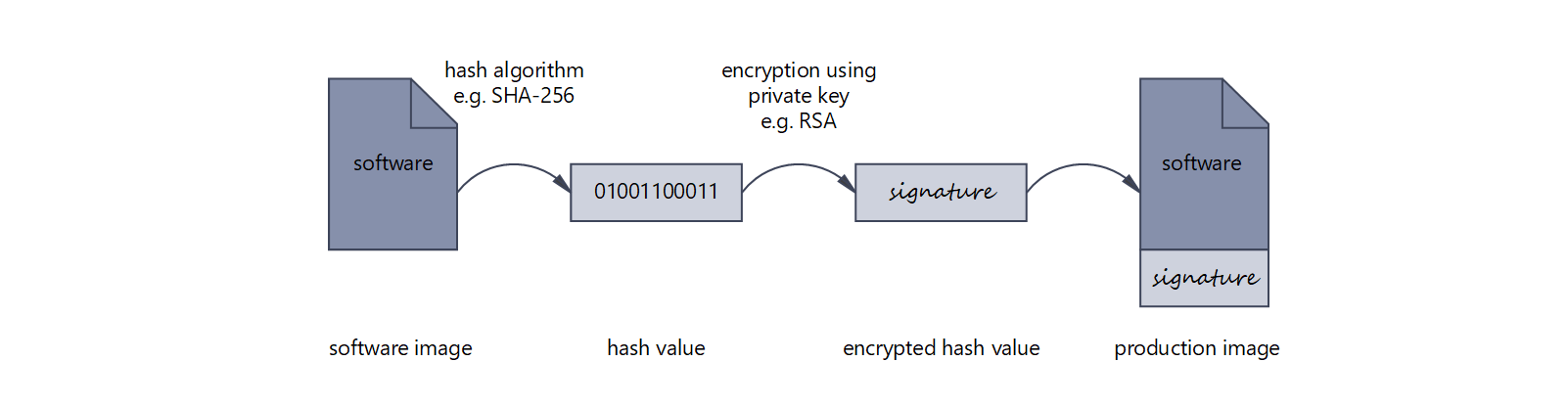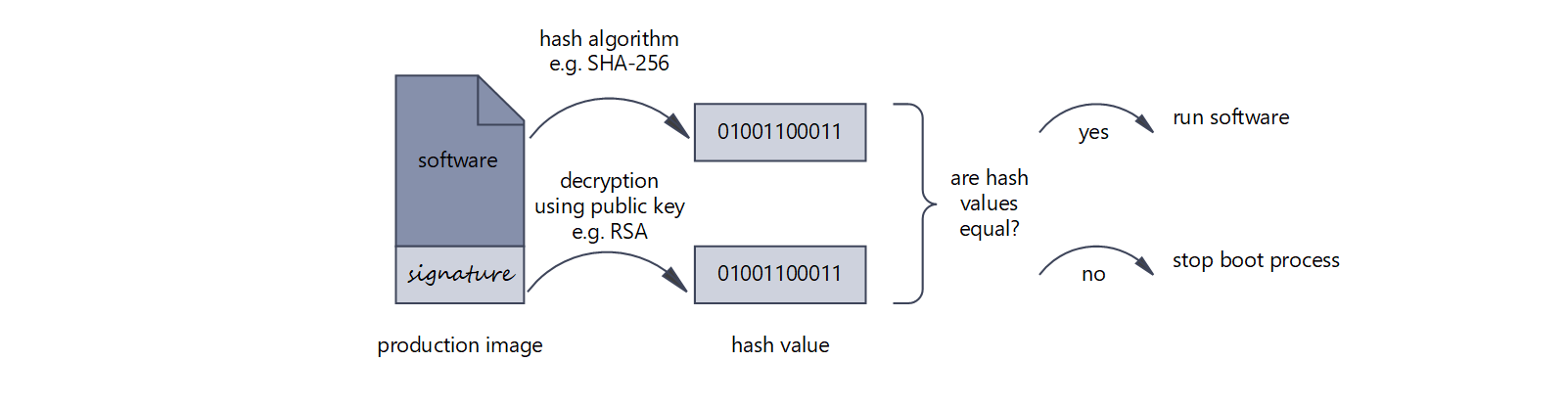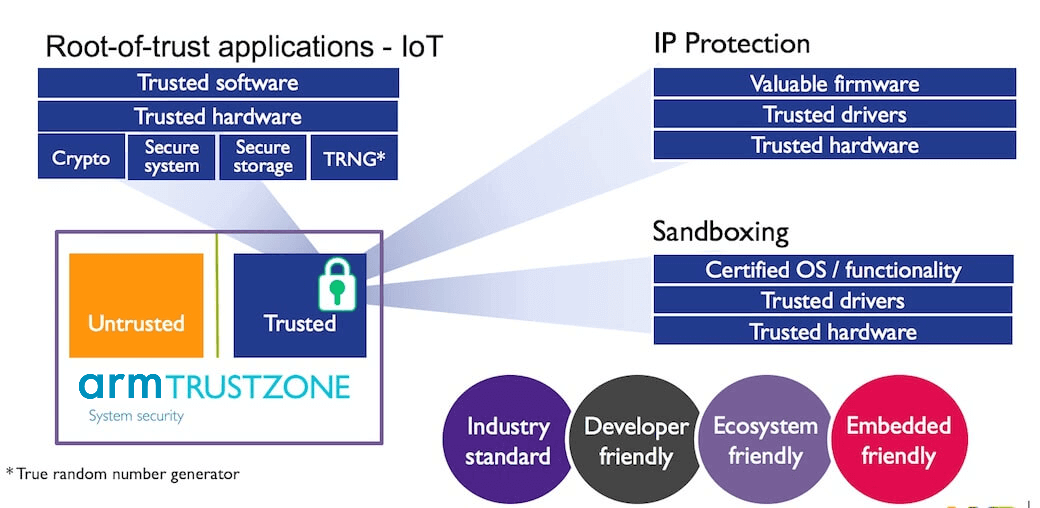
Designing secure embedded IoT devices - Architectures and Processors blog - Arm Community blogs - Arm Community

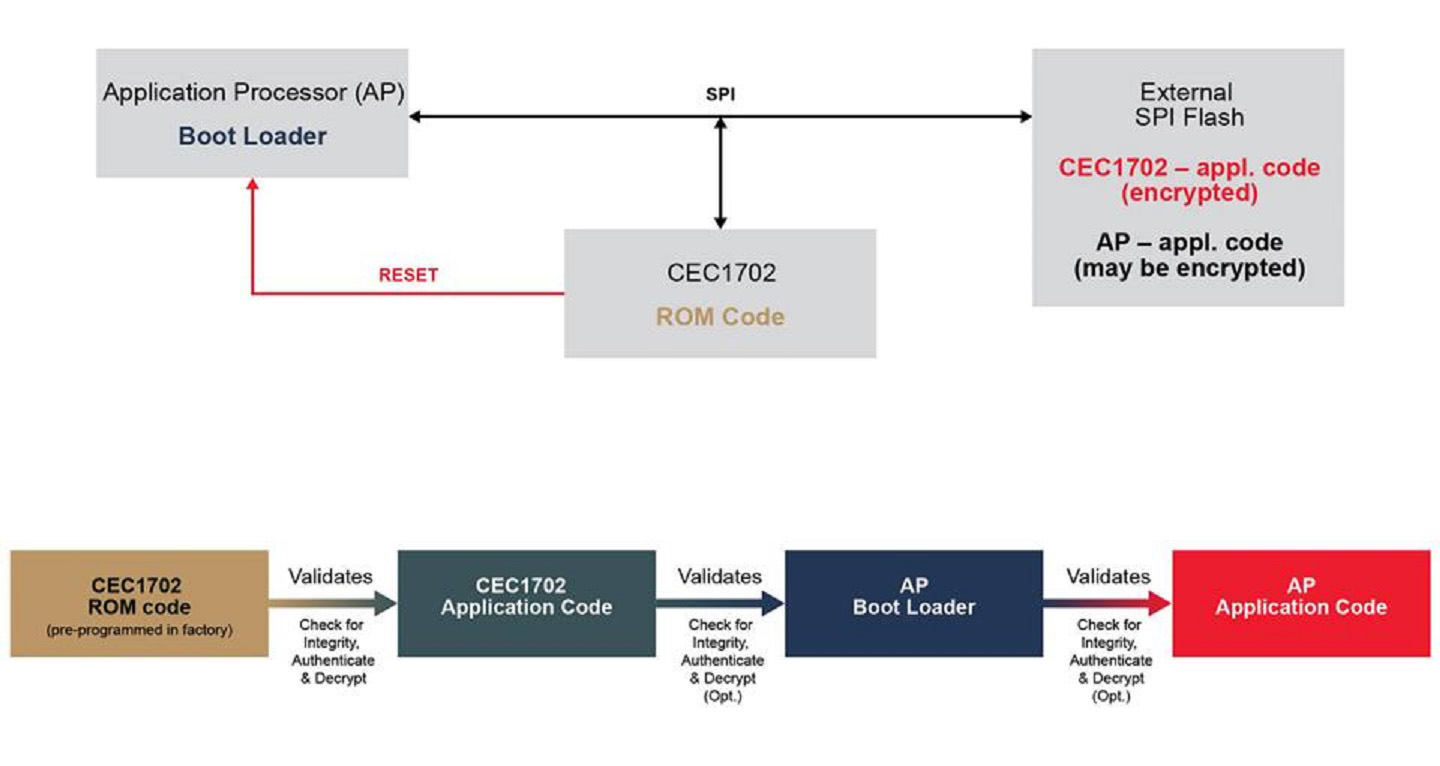
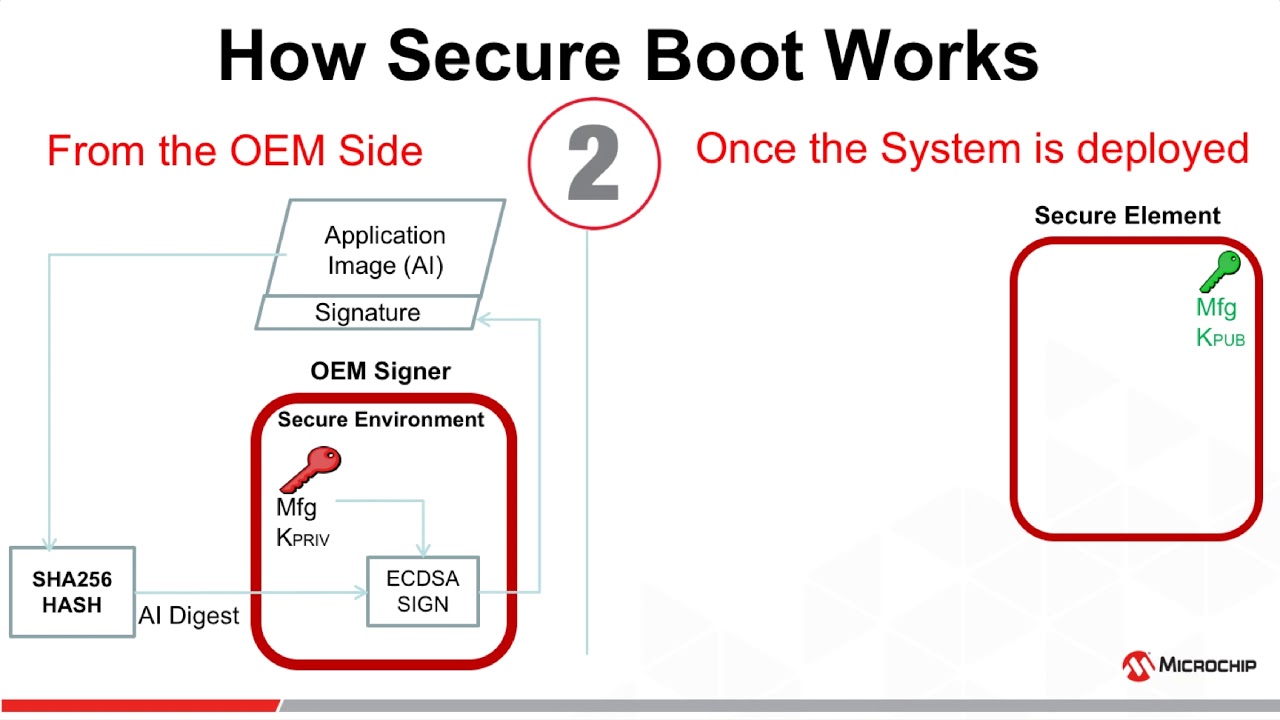
Secure Boot and Secure Download - Part 1: Protecting IoT Devices with Secure Authentication | Analog Devices
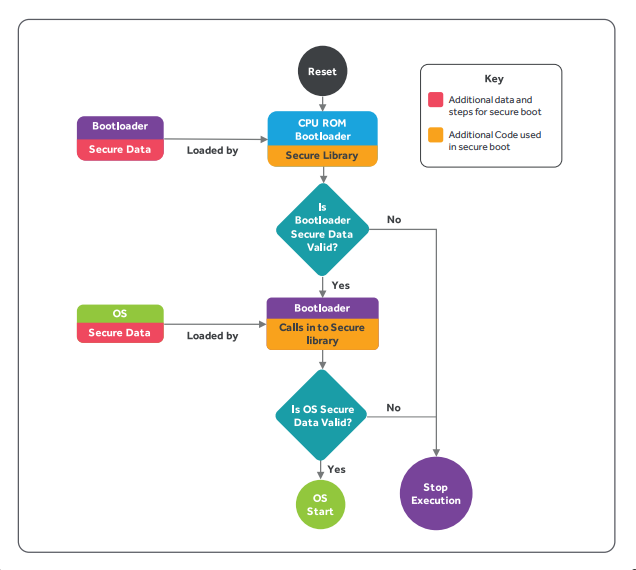
Build highly secure IOT device: secure boot, measured boot and attestation, secure storage etc | by lei zhou | Medium